Rapid technological advancement has spawned an exponential increase in connected devices, further facilitating communications on a truly global scale. However, the ever-increasing connectedness we experience as a society also has a dark side when it comes to digital security.
With a simple Google search we can compare flight prices, file for passports, learn how to build sustainable housing, and catch up on the latest news around the globe. But this access to information – to data – comes at a price. It has been said that data is the “new oil” of the information age. And with billions of connected devices comes billions of data sets on countless individuals, all too often left exposed.
Earlier this year, the FBI’s Internet Crime Complaint Center (IC3) reported a 300% increase in cybersecurity threats since the onslaught of COVID-19. According to the Center, complaint caseloads skyrocketed from an average of 1,000 cases per day to between 3,000 and 4,000 cases per day during the pandemic.
However, you may be surprised to find that individual hackers are just one facet of the problem.
This article will provide you with a wealth of information regarding the full scope of threats to digital security and personal privacy within the digital space. We will also provide you with a variety of actionable steps you can take to improve your digital security today.
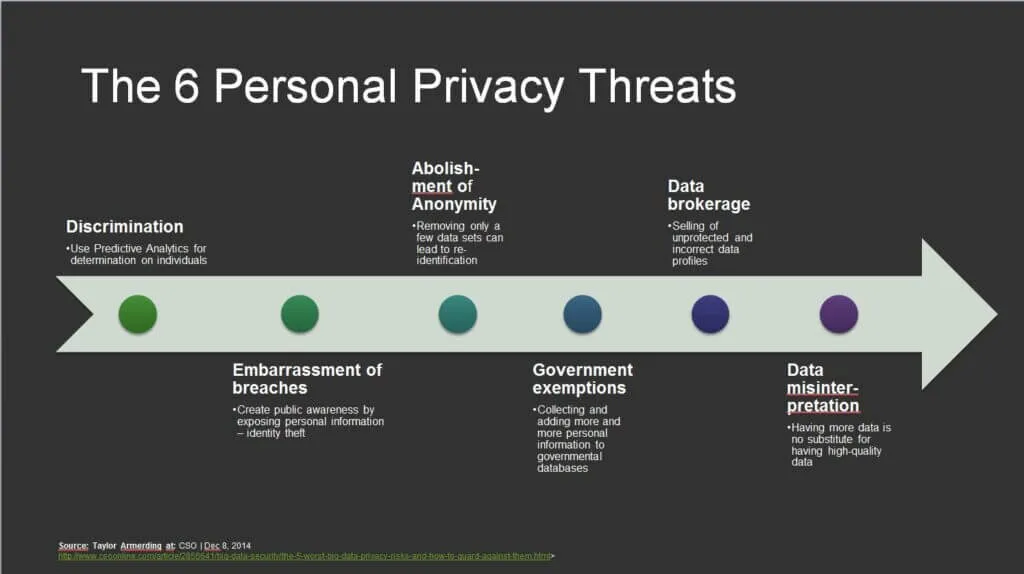
The Main Culprits in Digital Security: Big Data & AdTech
We’re all aware of the fact that each and every one of us can easily fall victim to a number of internet threats from hackers. Many of us have been schooled ad nauseam about various issues such as online scams, phishing, spam, and information mining. However, there is another side to internet threats that often goes unnoticed. The truth of the matter is that big data and AdTech are also largely considered enablers, and in many instances, perpetrators when it comes to threats on digital security and individual privacy.
Google’s history of privacy concerns
Google, along with many other big data platforms, has a long history of questionable practices when it comes to individual privacy and security. Earlier last year parent company Alphabet and the ad industry were singled out from a coalition of privacy activists for broadcasting consumers’ personal data without “proper security”. Data provided included sensitive information such as ethnicity, disabilities, sexual health and orientation and more. It was reported that the data was in fact “so sensitive” that it allowed advertisers to “specifically target incest and abuse victims, or those with eating disorders”.
Earlier this year the company was hit with a whopping $5 billion lawsuit for “illegally invading the privacy of millions of users” by tracking their internet use and collecting information about browsing histories even when browsers were set to ‘private’ mode. According to Search Engine Journal, the lawsuit “alleges that Google’s privacy controls are fake and that Google is illegally intercepting and selling private information.”
Facebook’s laundry list of privacy and security violations
It’s no secret that Facebook has a long and tawdry history of compromising consumers’ private information for the sake of advertising money. The public outcry began back in 2006 when Facebook’s News Feed was rolled out. Much to the dismay of many of the platform’s users, the company was broadcasting personal information, such as purchases people made to others without their knowledge. This wasn’t just shared with your friends; it was also shared with companies for advertising purposes.
In 2011 the company settled a suit with the FTC due to the fact that the platform failed to keep its privacy promises and allowed users’ private information “to be made public without warning”. A new revelation was made. If you, as a user, never authenticated a third-party app to collect your data, your private information could still be harvested simply due to the fact that your friends used a particular app.
In 2013 it was discovered that a platform bug exposed the private information, including the email addresses and phone numbers of over 6 million users to anyone who had a shred of contact information about someone.
To add fuel to the fire, there was the “Mood Manipulation Study” of 2014, issues with the platform’s ability to keep track of how many developers were using people’s previously downloaded data in 2015, and allegations from a Belgian court that Facebook was illegally tracking users data on third-party sites.
That’s not all. There was also a massive security breach in 2018 which exposed as many as 50 million accounts. It was then revealed that the platform was well aware of this data theft and failed to adequately warn its users.
Fast-forward to 2020 and the platform recently agreed to settle a class-action lawsuit to the tune of $550 million regarding its use of facial recognition technology. According to the suit, the company “violated an Illinois biometric privacy law by harvesting facial data” without user permission.
…And the list goes on
It almost seems as though we’ve become numb to the fact that various social platforms and search engines have a long history of compromising our personal data. But they’re not the only ones. One would hope that when they visit a government site or public health service, that their information would be handled with the utmost level of sensitivity. However, a 2019 report released by GDPR and an ePrivacy consulting firm found that more than “100 commercial companies” were “systematically and invisibly tracking” and collecting users’ sensitive data on sites such as these. This included information on sexual health, mental illness, physical illnesses, and pregnancy.
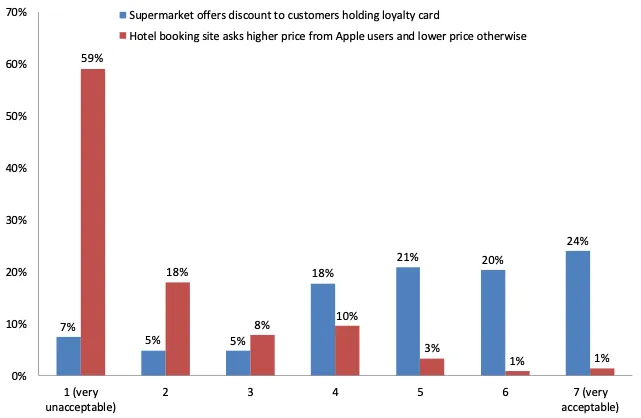
Algorithmic profiling, pricing discrimination, and niche scams
Algorithmic profiling at face value may seem rather innocuous. It is the process of collecting data, detecting patterns, and making predictions. However, research has found that corporations have a history of using this information in order to exploit and discrimination individuals as categorical groups. This type of information processing is used for pricing discrimination, where companies charge different prices for the same good or service to different groups of individuals.
Nathan Newman, author and research fellow at the New York University Information Law Institute described in detail how companies use algorithmic profiling for such purposes. Newman, who has a J.D. from Yale Law School and a Ph.D. from UC-Berkeley’s Sociology Department, found that big data and algorithmic profiling enables economic harm to vulnerable populations by empowering “a narrow set of corporate advertisers and others to prey on consumers based on behavioral profiling”.
The result is payday lender advertisers exploiting financially distressed households and offering subprime credit offers, or mortgage loan modification scams which target socioeconomically vulnerable populations.
For example, Wells Fargo came under fire in the early 2000’s for the company’s discriminatory practice of “illegally steering an estimated 30,000 Black and Hispanic lenders into more costly subprime mortgages”. That’s not all, the company also was found to be “charging them higher fees than comparable white borrowers”.
In 2011 Google’s CEO was hit with a $500 million lawsuit for “knowingly allowing illegal pharmacies to target users on its search engine”. These companies were, among other things, selling illegal steroids and fake subscription medications to sick individuals targeted through ads. To make matters worse, it was found that Google not only accepted their ads, but helped these “foreign-based pharmacies” write them for “maximum effectiveness”.
While there’s no denying the fact that targeted hacker attacks are a serious threat to digital security, it’s also crucial to remember that big data platforms and the AdTech industry have a long, well-documented history of unscrupulous behavior and enabling predatory practices.
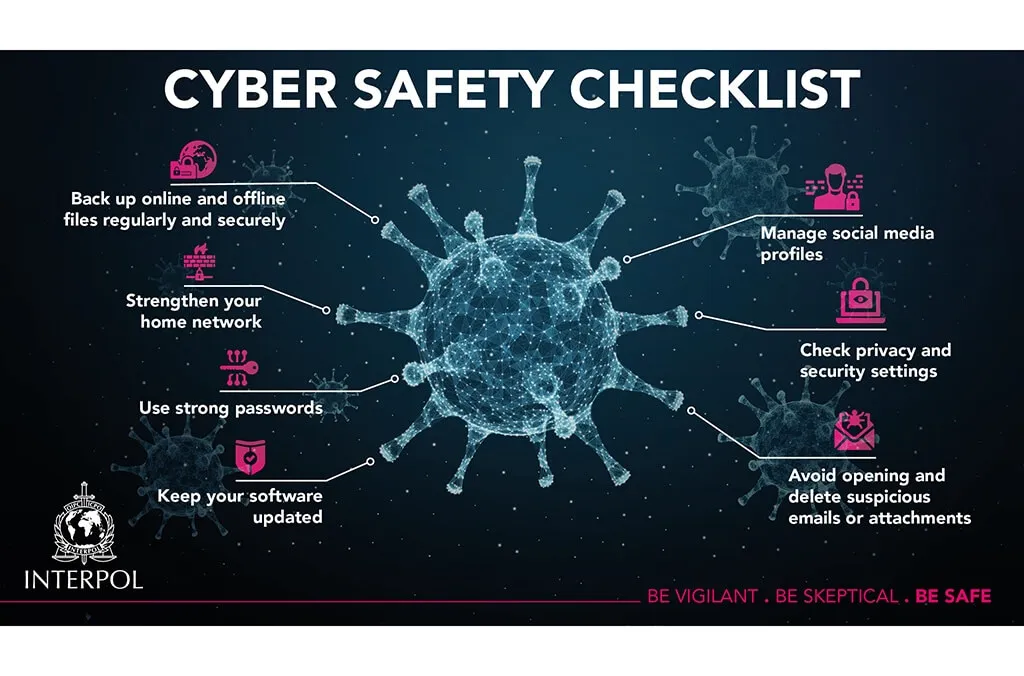
Improving digital security: Steps you can take to protect your private information
One can easily feel exhausted at the thought of taking appropriate measures in order to adequately protect their personal information online. Most of us have Facebook accounts, use Google’s search engine, shop online, bank online, and have a bevy of applications at our disposal to help streamline processes and facilitate communication. It’s bad enough that we have to thwart off attacks from individual hackers, but the idea that we’re also up against big data platforms and AdTech can be quite overwhelming.
However, the truth of the matter is that even the smallest steps can make a difference. In order to help you get started on your journey to improving digital security we’ve provided a list of six areas to focus on.
1. Clearing information caches
Information caches store data for the purpose of expediting the process of future requests for that data. Examples are pre-filled passwords, home addresses, and the ability to input your credit card information by simply typing the first few numbers and your card’s security code. However, caches also leave you extremely vulnerable to attacks, information harvesting, and identity theft.
As a result, it’s best to clear out cookie caches and browsing history on a regular basis. Programs such as Google Privacy Checkup can give you greater control over what data is stored on you and even provides you with the ability automatically schedule the deletion of data over certain periods of time. It can also show you which third-party apps have access to your accounts and allow you to revoke privileges at will.
2. Securing web browsing activities
There are several measures we can take into our own hands when it comes to improving digital security while browsing the web.
HTTP vs. HTTPS
For starters, know the difference between HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertex Transfer Protocol Secure). HTTPS uses a layer of encryption which helps foster secure connections between a browser and server. This is crucial when it comes to protecting your private information, especially when it comes to shopping online. The holiday shopping season is just around the corner. Be wary of inputting personal information on any websites without added security measures and be sure to check the URL for the ‘https://’ prefix.
Search engines
Everyone loves a personalized experience, and this is one reason why search engines, AdTech agencies, and companies work so hard to gather our personal data. Everything from our purchases to our browsing history and search queries are used to create profiles of us. Make use of security programs in the form of software or browser ad-ons that helps enhance privacy and security. Plug-ins such as HTTPS Everywhere, NoScript Security Suite, and Privacy Badger are popular options. If you’re looking to take it one step further, there are alternative search engine options available as well such as DuckDuckGo which offer private searching, site encryption, and tracker blocking features.
Public Wi-Fi
Public Wi-Fi is particularly precarious because users don’t need any authentication in order to access these networks. This makes it rather easy for hackers to conduct Man-in-The-Middle (MiTM) attacks where your activity and data can be quietly surveilled and stolen without your knowledge. Many hackers even set up fake Wi-Fi spots mimicking popular retail ones.
In general, it’s best to forego public Wi-Fi altogether. If you must use it, you should absolutely refrain from accessing any platforms containing highly sensitive information such as your banking institution. Instead, set up your phone as a hotspot and use your 4G/5G/LTE connection instead.
VPNs
Virtual private networks have recently become mainstream as they facilitate a secure connection between browsers and servers. If you work for a large organization, chances are they may require you to use a VPN in order to access their resources remotely. When choosing VPNs, bear in mind that you get what you pay for as premium services often come with greater peace of mind, improved browsing experiences and broader bandwidth capacity.
3. Beefing up online account security
Passwords
You’ve heard it a million times and you’re going to hear it again: Complex passwords are your frontline of defense when it comes to keeping your online accounts safe. Never use the same password for all of your accounts and refrain from including things such as date of births, pieces of your social security number, and other sensitive information in them.
If you find that you’re having too much trouble remembering them all, password managers and vaults can help. If you’re looking for a list of credible vendors, CNET has a wonderfully useful password manager directory you can browse.
Two-Factor Authentication (2FA)
Two-Factor Authentication is one of those added layers of security that we all love to hate. After all, we live in a world designed to fulfill our voracious need for instant gratification and the very prospect of having to jump through multiple hoops to sign into something often leaves us with a bad taste in our mouths. But, alas, it’s necessary. Many platforms offer this as an added layer of protection, however there are also standalone options such as Google Authenticator and Authy available.
4. Encrypting online communications
Far too many individuals, employees, CEOs and companies have fallen victim to hackers who have targeted their communications. Whether it’s your personal email, work email or SMS, taking a step to encrypt your online communications is critical. OpenPGP touts itself as “the most widely used email encryption standard” and Keybase.io is popular for secured messages and file sharing. When it comes to mobile communications, WhatsApp has also achieved global popularity as an alternative messaging solution. Those interested in taking online communications a step further can consider solutions such as TempMail, which offers anonymous, secure, temporary email addresses which safeguard you against tracking, spam, advertising emails, and hacking robots.
5. Improving mobile security
In a world where mobile phone browsing is quickly overtaking traditional desktop browsing, mobile security is key. While your phone may provide you with a secondary layer of protection when it comes to 2FA, it can also serve as a weak link in the chain. As a result, it is recommended to always stay on top of the latest patches by regularly checking your device for updates. Use biometrics such as FaceID or TouchID if your device allows it, or other functions such as passcode and pattern lock in order to prevent physical compromise. It is also recommended to disable location services on your mobile devices and to register your devices with tracking solutions such as Apple’s Find My iPhone or Google’s Find My Device.
When it comes to mobile apps, it’s important to only install ones from reputable vendors and to keep track of the number of applications you provide with your information. It’s far more common than one would imagine for shady organizations to set up applications solely for the purpose of installing malware or spyware onto your mobile device in order to harvest sensitive information. Don’t throw caution to the wind, and make sure to install a reputable antivirus mobile software solution in the app stores such as McAfee’s Mobile Security app or Norton’s Mobile Security app.
6. Reducing your digital footprint
Years of activity on the world wide web can catch up with you. The truth of the matter is that many of us are wholly unaware of the vast amounts of data which are circulating around on the internet about us. However, there are steps you can take to reduce your digital footprint.
First, you want to delete or deactivate any old or unused shopping accounts, email accounts and social network accounts. In general, it is ideal to use “burner” information when setting up accounts such as throwaway email addresses and fake personal information such as names, addresses, and dates of birth.
Second, avoid filling out surveys. This is especially the case when it comes to those cute little online quizzes we all too often see buzzing around social media platforms which ask you to post information such as your mother’s maiden name, date of birth, your hometown, your first pet’s name, etc. These are the same questions that are often posed on secure accounts to verify one’s identity and are often gleaned in seemingly innocuous ways for information mining.
Fortunately, there a variety of robust solutions available to those looking to clean up their digital footprint. Premium services such as DeleteMe come at a cost, but are effective in removing personal information from data broker websites and Google search results. Troy Hunt’s Have I Been Pwned is also a popular solution for checking whether your email accounts have been exposed due to data leaks. There are also corporate solutions such as ReputationDefender which are great for reputation management purposes.
Conclusion
Improving your digital security can quite easily seem like a daunting task, but it’s important to remember to take the process one step at a time. Each and every step you take is another brick added to your wall of defence against the myriad of hazards lurking within the digital space. Use this article as a guide to better understanding the full scope of threats to your digital security so that you can stay one step ahead and safeguard yourself against privacy invasion and attacks.
The holiday shopping season is officially upon us! Are you taking measures to improve digital security and protect yourself or your company against threats? Contact us today to learn more about our suite of tools and services which can help you get started on your path to a more secure digital presence.
Sources:
- How Big Data Enables Economic Harm to Consumers
- Cookiebot GDPR compliance report
- Cybersecurity 101: Everything on how to protect your privacy and stay safe online
- Google and Ad Industry Accused of “Massive” Abuse of Intimate Personal Data
- Google faces $5 billion lawsuit in U.S. for tracking 'private' internet use
- Google faces lawsuit over tracking in apps even when users opted out
- Google Faces New Class Action Lawsuit for Privacy Violations
- Facebook to Pay $550 Million to Settle Facial Recognition Suit
- A timeline of Facebook's privacy issues — and its responses
- Facebook Manipulates Our Moods For Science And Commerce: A Roundup
- Why taking Facebook quizzes is a really bad idea
- FBI sees spike in cyber crime reports during coronavirus pandemic
- REDUCING YOURDIGITAL FOOTPRINT
- Cybersecurity Best Practices

%402x.svg)




%402x.svg)

