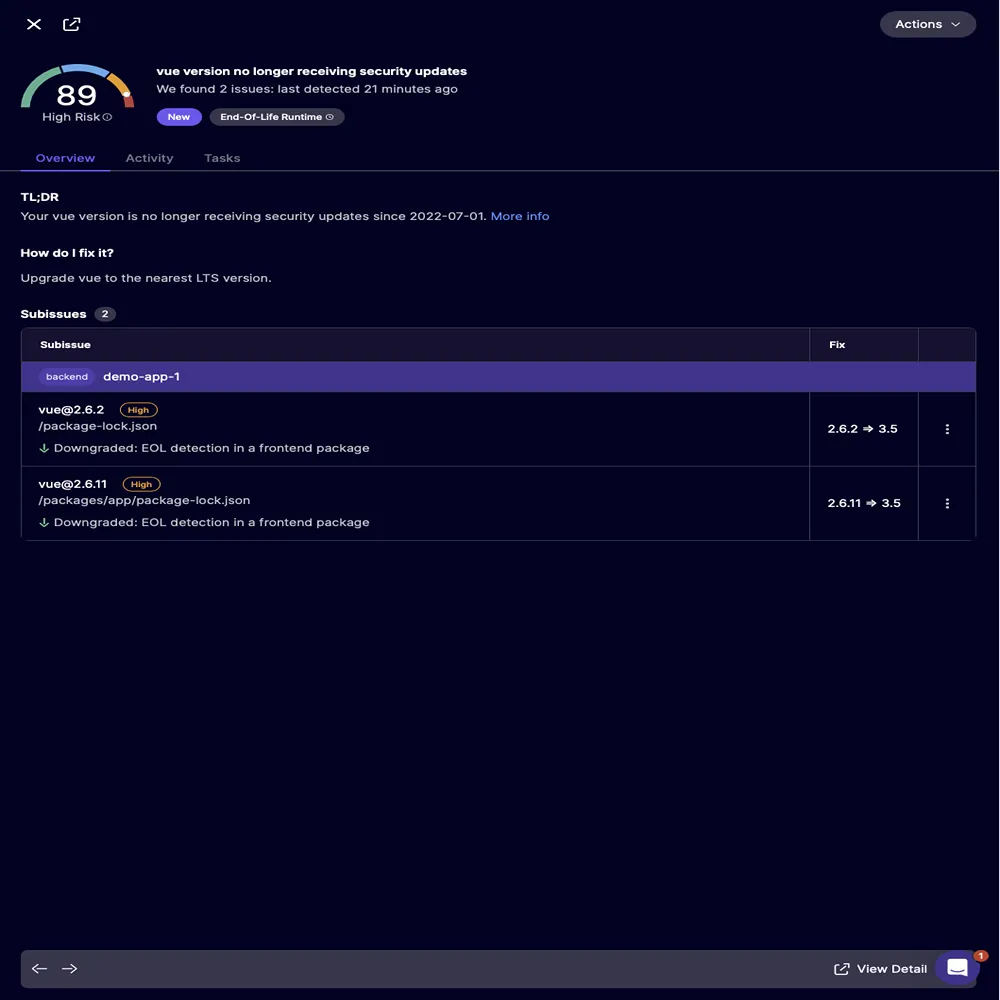
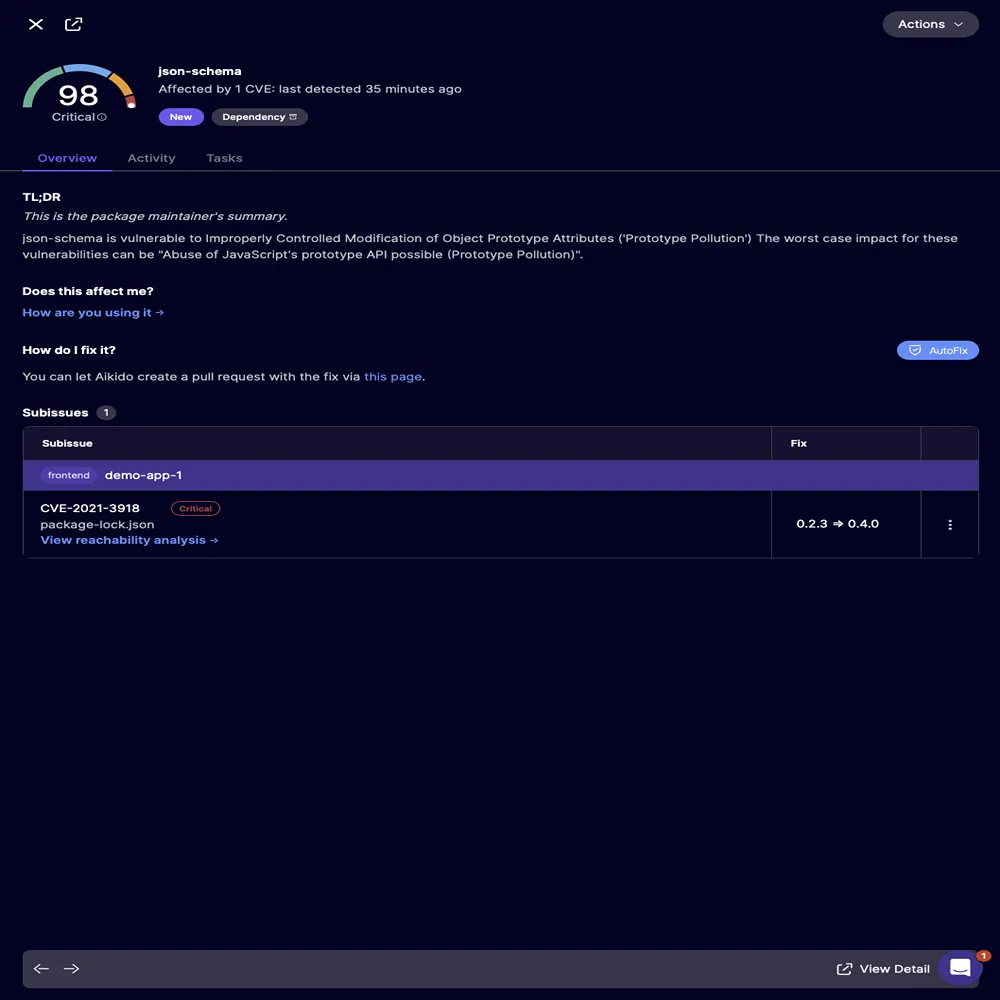
Aikido

For years, software teams have been haunted by a silent, unspoken dread, dealing with old code. Every engineering department has that one legacy module created by someone who left the company five years ago, that one controller file bloated to a thousand lines, that one database utility that still relies on functions that were outdated before some interns were even born. Modernizing it meant spending days sifting through documentation, conducting line-by-line reviews, cross referencing functions, resetting API keys, re-architecting half the pipeline, and hoping nothing broke in production. Most developers simply steered clear of the task until a bug, vulnerability, or major version update forced them to confront it.
Yet something has shifted in the past few years. The emergence of automated security and modernization platforms, with Aikido being one of the most impactful, has subtly changed how engineering teams tackle legacy systems. Instead of wading through a never ending mire of outdated dependencies, insecure functions, and hardcoded secrets, developers now gain immediate insight, precisely what is wrong, exactly where it is located, and how to fix it. This change has sparked one of the most significant transformations in the modernization process.
Nowadays, modernization feels less like digging through the past and more like performing assisted surgery clean, precise, and predictable. The fear is diminishing, and a newfound confidence is emerging. The tools don’t magically resolve every issue, but they shine a light on the path so clearly that what used to take weeks can often be addressed in just minutes.
To understand how this situation arose, picture a standard modernization day. A developer starts working on a project from 2018, using Laravel 6, PHP 7.2, some old jQuery scripts, and a set of controllers that seem like an attempt to cram three microservices into a single monolithic application. As soon as the repository is scanned, the platform kicks off the process of mapping its entire structure. In just a few seconds, it presents a dashboard that resembles a medical chart for a codebase, highlighting deprecated helpers, outdated packages, hardcoded credentials, weak hashing, exposed endpoints, missing security headers, and unvalidated input. Years of accumulated technical debt are distilled into a clear diagnostic overview.
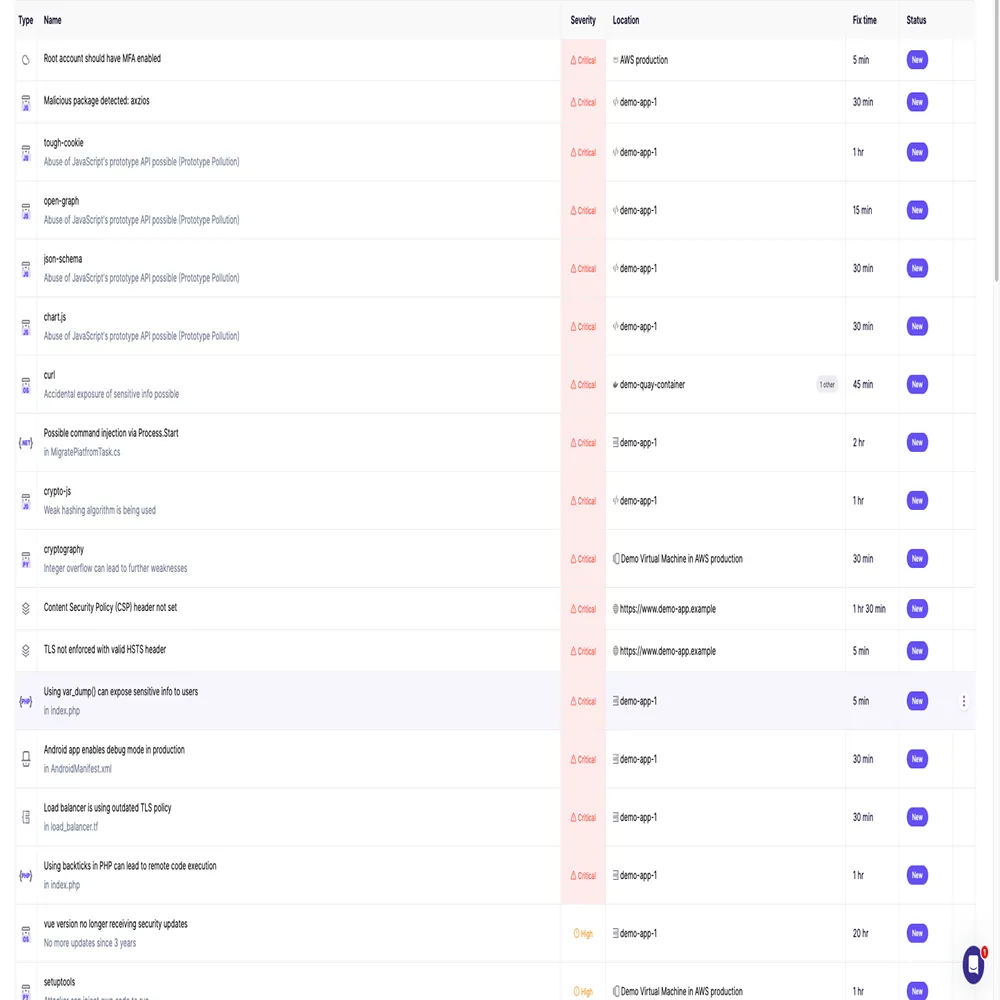
One of the biggest changes these platforms offer is how they turn uncertainty into clarity. Rather than having developers hunt down outdated functions like str_random(), array_get(), and unsafe redirects, they can instantly view highlighted alerts along with modern, secure alternatives. What used to involve sifting through upgrade manuals and StackOverflow discussions now shows up in a contextual, almost interactive format.
A standard automated detection could look something like this,
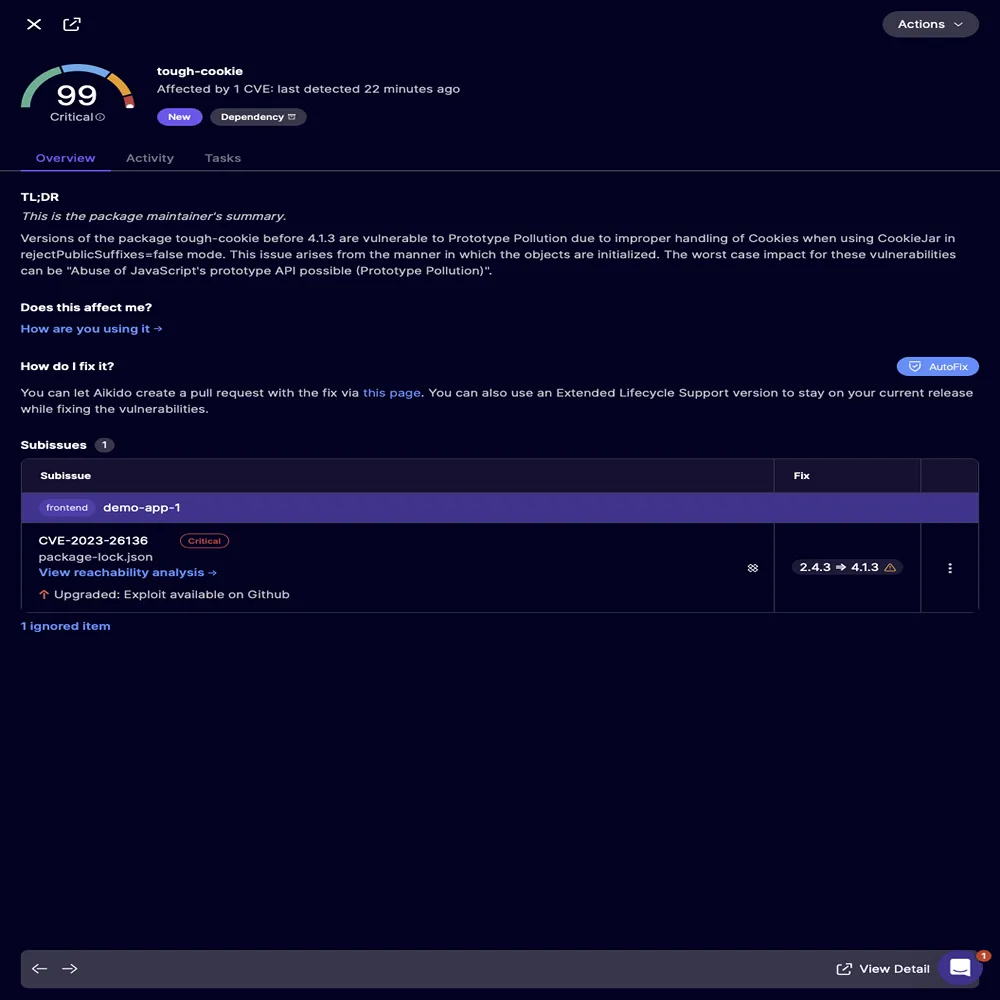
This is not just a simple lint warning. Its the essence of modernization, grasping the old pattern, creating its updated version, and positioning it precisely where it should be. The time it saves for developers is beyond measure, not due to the complexity of the change itself, but because finding the problem used to involve a person manually sifting through thousands of lines of code.
However, the true strength comes when these platforms do more than just point out problems, they fix them. Take the outdated database code thats often found in older PHP applications. A developer might come across this typical, vulnerable snippet.
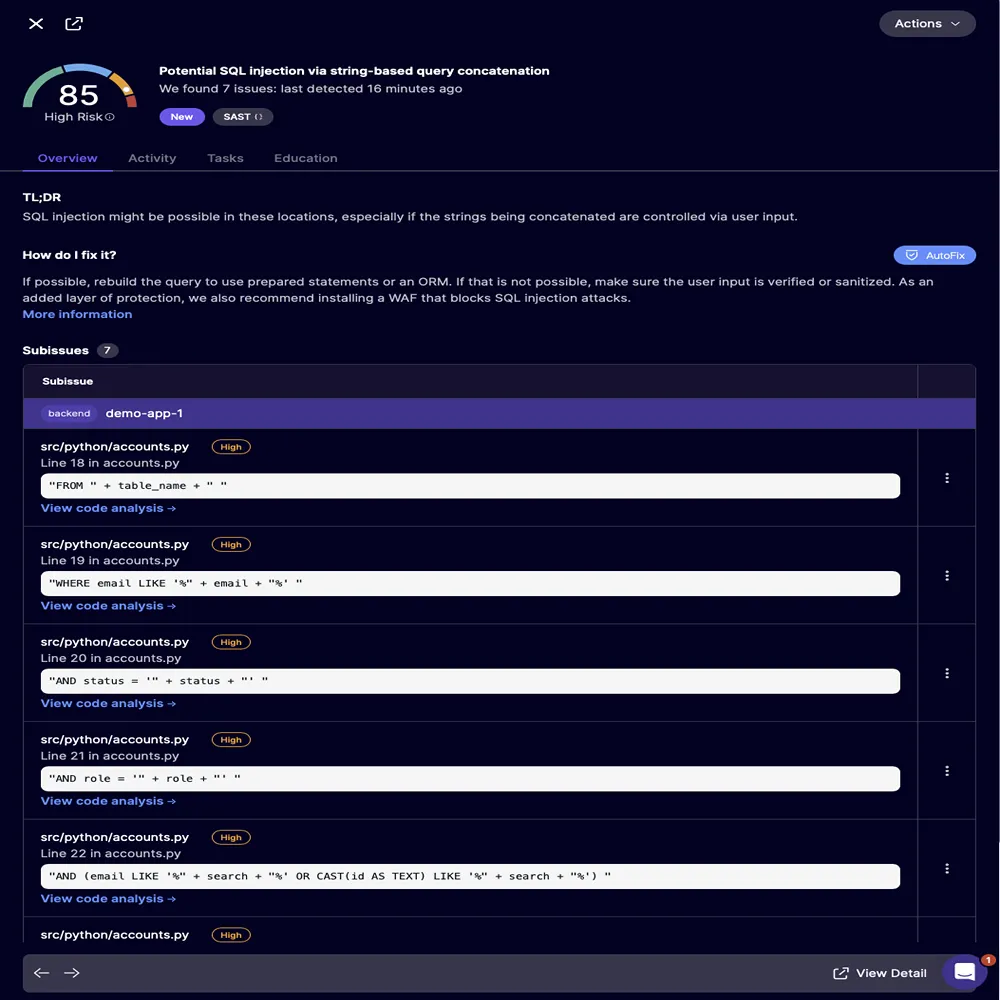
Previously, rewriting this into a secure, modern version using prepared statements required awareness of SQL injection risks, knowledge of parameterized queries, and enough time to carefully replace each instance. Today, the platform detects the vulnerability and instantly offers a patch, function. The process of modernization shifts from being a massive overhaul to a step-by-step transformation, with each fix being automatically validated.
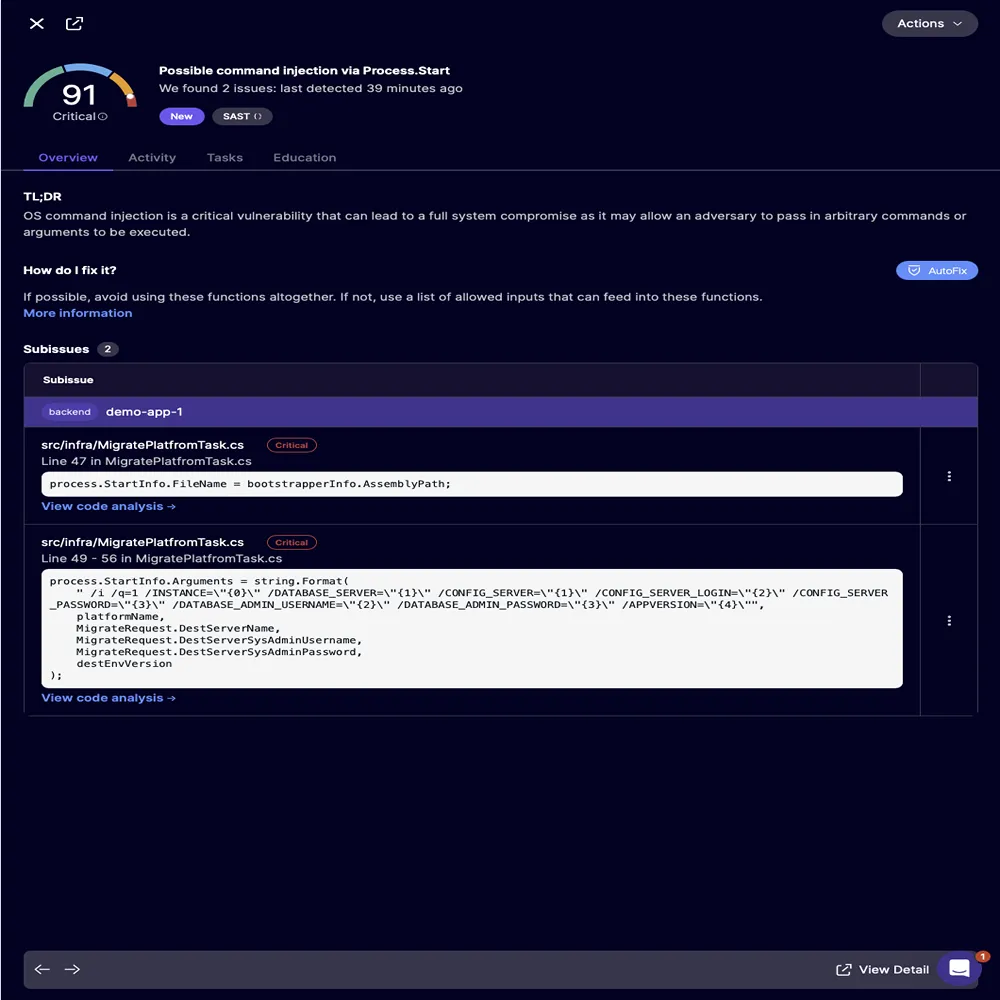
Modernization also used to involve a nightmare of dependencies. Old packages resulted in broken APIs, version conflicts, and hidden incompatibilities that only showed up after deployment. Nowadays, tools analyze composer.json or package.json to not only spot outdated packages but also predict the effects of updating them. A standard output resembles a small-scale upgrade strategy.
A developer does not have to read a 4000 word changelog. The platform has done it for them. It interprets the differences, analyzes actual code usage, and presents changes in human readable form. The modernization becomes faster, yes but more importantly, safer. Unseen incompatibilities are the true enemy of upgrade cycles, and these tools neutralize them before they strike. Another area that has radically changed is secret detection. Every long lived repository eventually accumulates questionable artifacts: test API keys, temporary AWS secrets, hardcoded tokens left just for debugging, and even entire credential files mistakenly committed. Traditionally, discovering these required manual greps, code audits, or worse post breach investigations.
Now, the moment the platform scans the repository, it highlights secrets instantly, even from deep within commit history. A detection might appear like this:

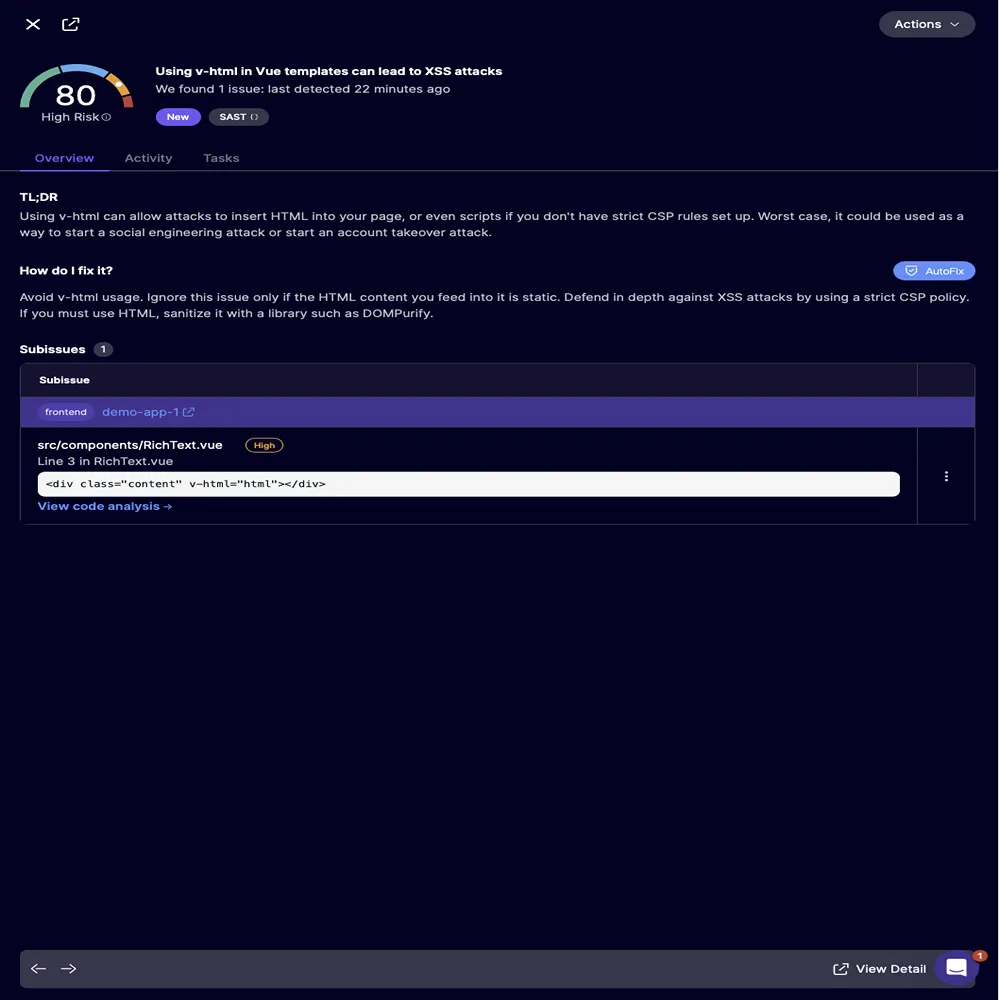
This type of modernization used to take a long time, often involving rewriting git history and invalidating old keys. Now, it happens almost instantly. Security headers are another often overlooked aspect of modernization that automated tools have greatly improved. Most developers don’t like the task of writing complicated CSP rules, setting up HSTS, or activating Permissions-Policy directives. These headers usually need a thorough understanding of how browsers work, the latest best practices, and possible scenarios where things could break.
Older applications seldom include any of these headers. However, with just one analysis pass, a platform can spot missing headers, automatically create modern configurations, and clarify exactly where they should be placed in the codebase.
Before modernization:
- No HSTS.
- No CSP.
- No secure cookies.
- Full attack surface exposed.
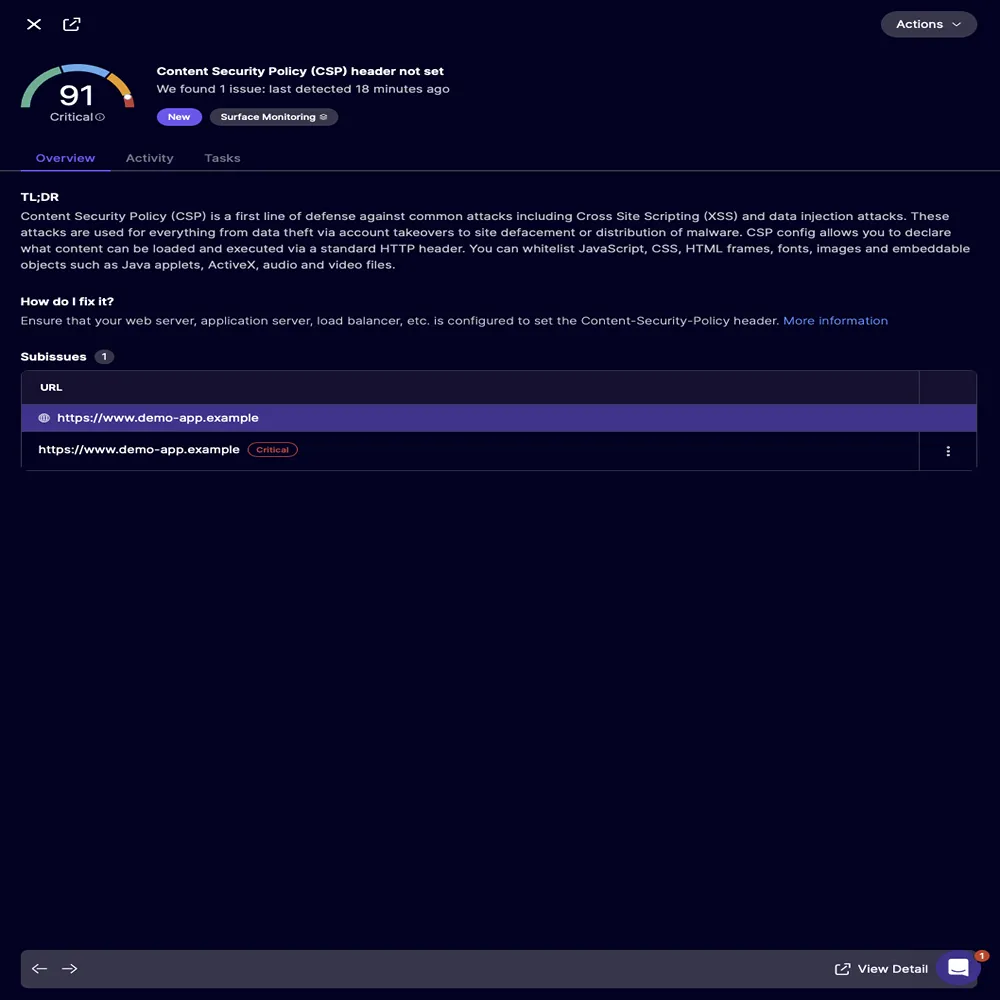
After automated guidance:
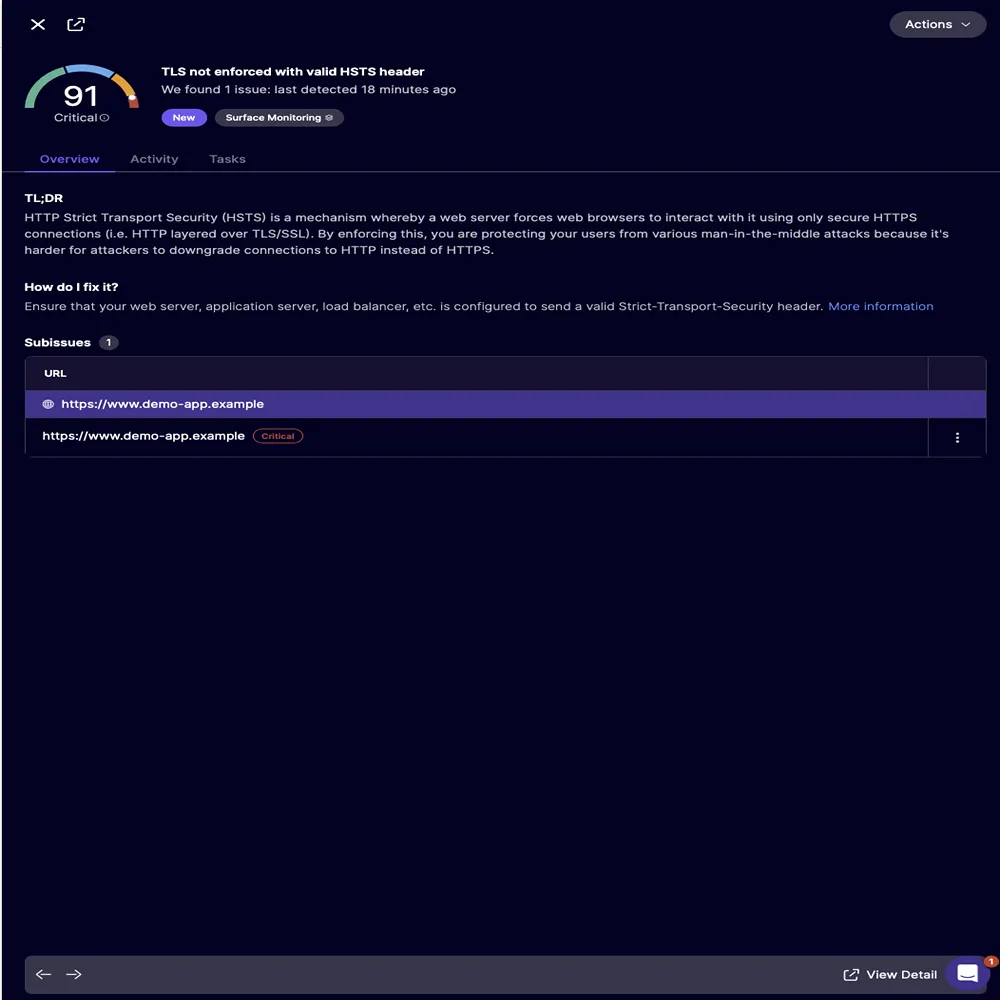
What used to be a specialized task handled only by senior security engineers becomes accessible to every developer, instantly improving the security posture of even the oldest applications.
The modernization also extends into authentication systems. Many older codebases still rely on weak hashing algorithms such as MD5, SHA1, or even low-cost bcrypt settings. These are now detected immediately, with suggested upgrades to Argon2ID or higher cost bcrypt configurations. The modernization snippet appears clearly and contextually:
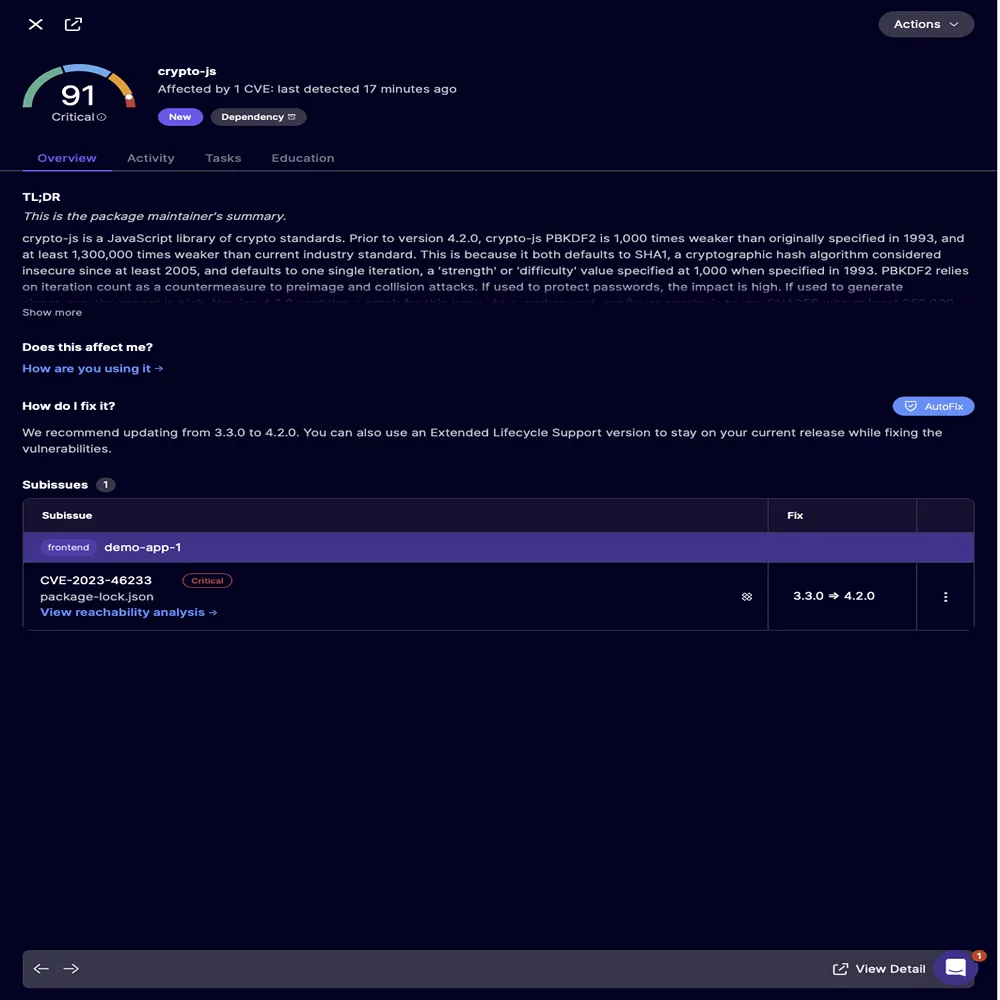
Instead of developers guessing what “modern hashing” means, the platform injects the exact, highest-standard form directly into the project.
As these kinds of improvements compound dependency upgrades, secret removal, vulnerability fixes, header enhancements, hashing upgrades another invisible benefit emerges dead code begins floating to the surface. Modernization is not only about replacing old patterns but also about trimming unnecessary bloat. Automated platforms map unused classes, uncalled methods, orphaned controllers, and routes that haven’t been triggered in months. In old projects, this can easily remove hundreds of lines and dozens of files.
Modernization becomes clean. Lean. Efficient.
However, the most significant change is in the major framework upgrades. In the past, transitioning from Laravel 8 to Laravel 11 or from Node 12 to Node 20 was a challenging process. Developers had to manually check upgrade guides, rewrite route syntax, update factories, replace helper functions, and test for compatibility, all while hoping that nothing would break silently. Now, platforms can analyze the entire project, create a comprehensive step-by-step modernization plan, and point out every breaking change.
A modernization map could resemble a migration story:
- Old helpers identified and replaced.
- Legacy factories upgraded to class-based versions.
- Deprecated routing syntax rewritten.
- String functions swapped with Str:: methods.
- Middleware standardized.
- Controllers updated with new signatures.
And all of this comes with context aware explanations so developers understand exactly why the change is important. The modernization process itself turns into a learning experience.
The final, subtle change is continuous modernization. Previously, modernization was a one-off event. A team would upgrade the project, test everything, deploy it, and then move on until the next issue arose. However, automated platforms now continuously scan for new vulnerabilities, patches, deprecations, and dependency risks. When a package becomes insecure, when a vulnerability is found in a library, or when a new version brings breaking changes, developers are notified immediately.
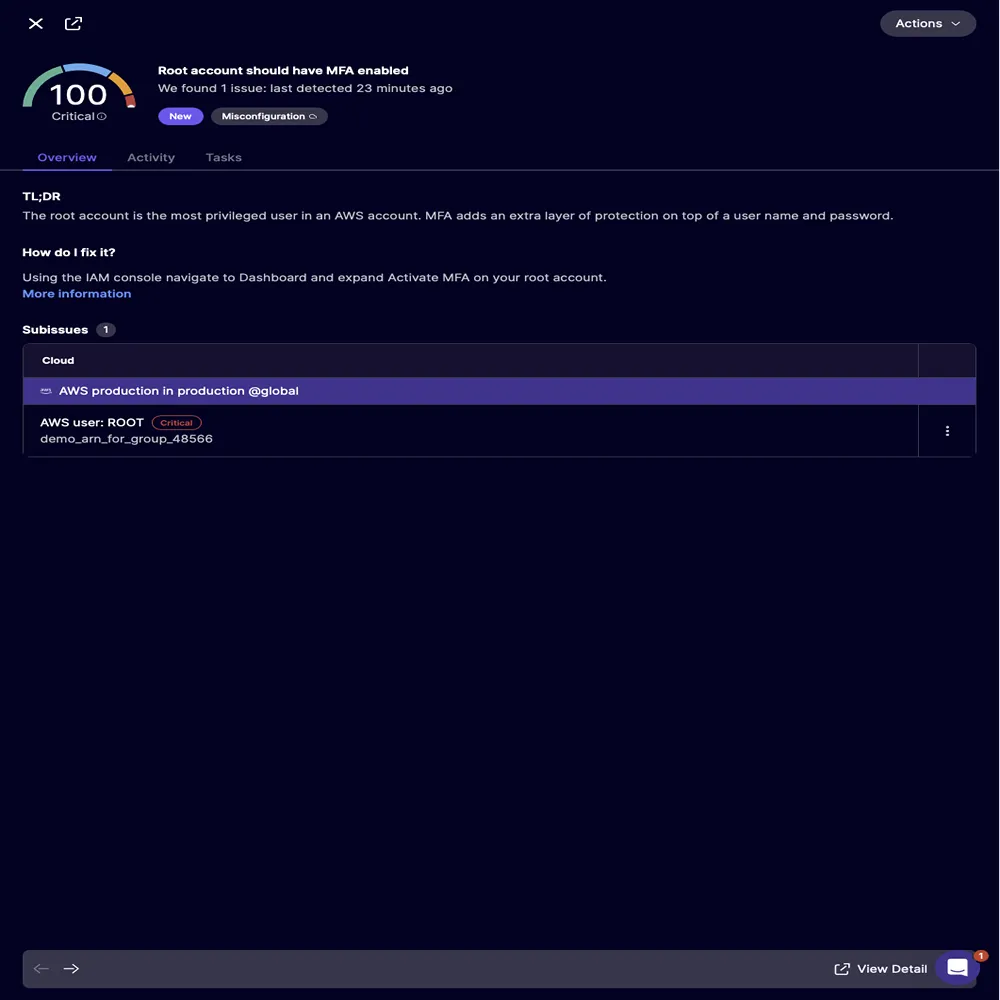
A modernized codebase remains contemporary. It does not revert back to outdated systems.
It's hard to emphasize enough what this change means for engineering teams. Historically, modernization has been one of the most feared aspects of software development. It used to be slow, costly, unpredictable, and risky. Nowadays, its quick, safe, clear, and well-directed. Teams are able to dedicate more time to developing features and less time dealing with legacy problems. Junior developers can confidently work within older systems. Senior developers can concentrate on architecture rather than just rewriting syntax. Security and development are now more integrated than ever.
Platforms like Aikido are not replacing developers, they are eliminating the obstacles that made modernization difficult, hazardous, and endlessly postponed. They illuminate the darkest areas of a codebase and turn modernization from a burden into a standard practice.
By doing this, they are not only modernizing code, but they are also transforming the entire process of building, securing, and maintaining software. The future is for teams that can act swiftly without causing issues teams that can upgrade boldly, patch immediately, and maintain secure foundations with ease. Automated platforms are paving the way for that future.




