Modern Defense

Modern Defense
At its essence, security isn't just one practice or tool. Its about gradually building an understanding and sharpening awareness through countless quiet moments where we notice details that others might overlook. It grows from repeated experiences with systems, broken parts, unexpected problems, and patterns that keep showing up. Over time, this familiarity becomes the quiet force that helps guide secure modernization. Real security doesn't come from random events or tools; it develops slowly from thousands of subtle observations, small improvements, and ongoing interactions with changing technology. Its a discipline that quietly grows in the background, affecting decisions even before we are fully aware of them.
Every secure, modern system has a long history of decisions, corrections, discoveries, and insights that support its stability. There are times when something unusual in the log’s hints at a deeper problem; times when a minor fix reveals a long-hidden flaw, times when a previous mistake subtly shapes how the next feature is created. Each of these moments adds to an internal database of intuition a sense of what is safe, what is risky, what needs to change, and what should stay the same. This quiet development is what enables modernization because modernization isn't just about updating code; it's about understanding what should change, how it should change, and why those changes are important.
It resembles the growth of a tree.
The main trunk symbolizes the familiarity that develops over time, an instinct created by facing problems repeatedly, picking up on subtle hints, sensing where issues might arise, and grasping how systems react under stress. It remains strong not because it was planted recently, but due to years of enduring various conditions, failures, and improvements. The trunk is stable and rooted, molded by everything that has happened in the past. Its strength is shown in its adaptability: how it has coped with significant changes, urgent fixes, sudden outages, and evolving threats. This central structure influences how confidently modernization efforts can proceed. Each outdated function that gets replaced, every old library that gets updated, and every insecure pattern that gets eliminated all contribute to the trunk. The understanding of what modern code should entail is not just theoretical; it is developed through layers of ongoing refinement. It expands through experiences with legacy systems, learning which areas are prone to breaking during updates, observing how older components react to new conditions, and identifying the points where architecture needs to change. The trunk grows thicker with every system migration, every refactor, and every code review that calls for more clarity and improved structure. From the trunk, branches extend outward in various directions. These branches symbolize enhanced skills the ability to analyze code clearly, quickly spot risky patterns, comprehend the effects of changes, and foresee where vulnerabilities might lie. Together, they create a dependable network of problem-solving pathways. These skills do not develop all at once; they grow gradually, driven by necessity, and are shaped each time an unexpected problem pushes the system beyond its comfort zone.
As branches develop, they change by adapting to new technologies: fresh languages, updated frameworks, new backend systems, modern cloud platforms, and evolving security threats. They embrace the shift from older coding practices to contemporary standards, transitioning from procedural methods to structured designs, from outdated hashing techniques to more robust algorithms, from flexible inputs to strict validation, and from monolithic structures to modular or distributed architectures. Branches also signify the growth of knowledge from basic functionality to more complex aspects like performance, scalability, reliability, and security. Each branch illustrates how modernization impacts the overall integrity of the system. Updating a library isn't merely a technical task; it involves anticipating how that update will interact with existing components. Refactoring a function goes beyond just cleaning up code, it is a choice based on understanding which patterns may lead to future instability. Enhancing authentication isn't simply about adding security; it requires recognizing that users need to navigate the system smoothly. Every branch contributes to structure, direction, and reach. However, even a sturdy trunk and wide branches cannot thrive without nourishment. This is where the roots come into play, drawing in everything necessary to transform understanding into action.
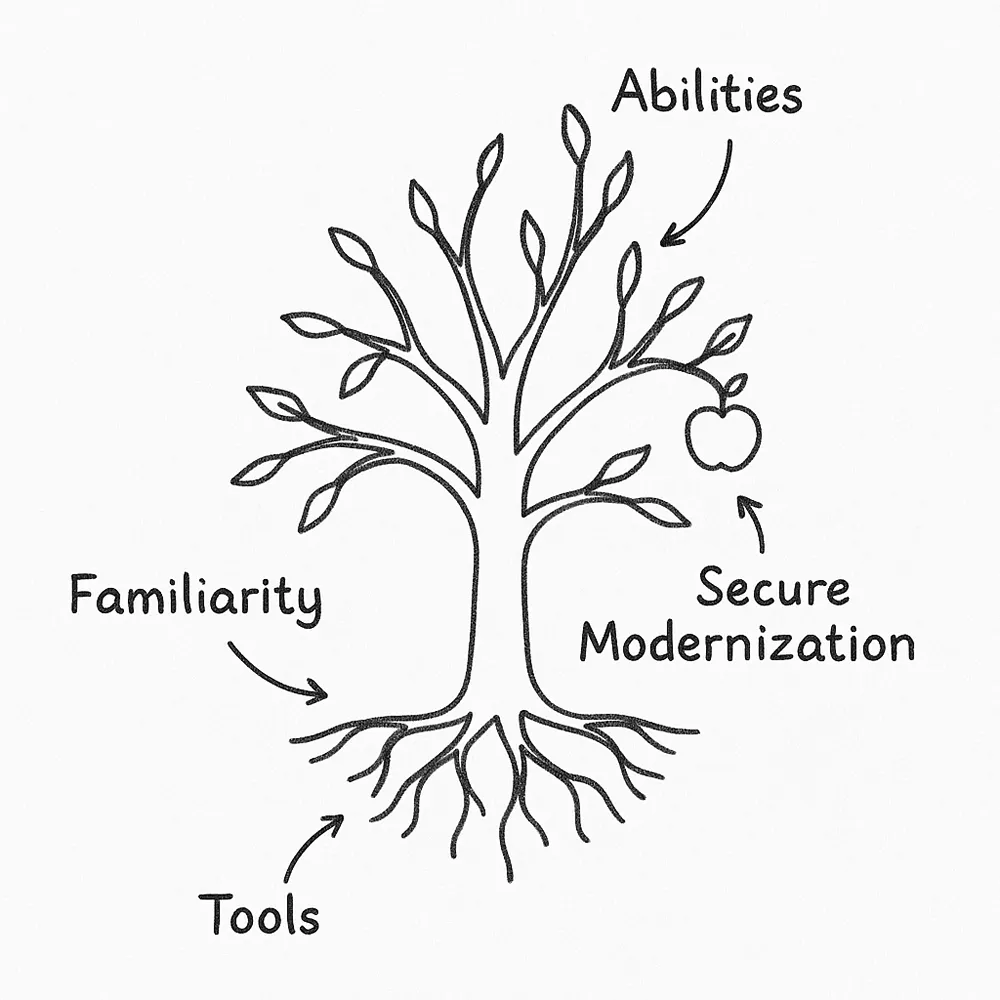
Tools such as Aikido, Swimm, and Heimdal provide essential support. This is precisely where code modernization comes into play. Aikido functions like clear water that seeps into the roots, uncovering unsafe code, outdated components, insecure dependencies, leaked secrets, and misconfigurations as they arise. Each alert improves internal understanding by pinpointing what requires attention. Aikido doesn't merely flag vulnerabilities; it also brings to light outdated functions, deprecated libraries, unmaintained frameworks, weak hashing algorithms, unsafe code constructs, and structural problems that hinder modernization. Thus, modern security scanning transforms into a guide for modernization. Every detected issue represents not just a risk but also a cue for where the system needs to grow. When a vulnerability is found in a package that hasn't been updated for years, it highlights the necessity for dependency modernization. If a weak algorithm is discovered, it indicates where cryptographic modernization is needed. When unsafe patterns are identified, it shows where the system must adjust to meet modern coding standards. Aikido serves as the lens that uncovers the modernization roadmap hidden within the codebase. Swimm acts like sunlight filtering through the branches, providing structure to codebases, clarifying complex processes, and preserving vital information for future tasks. It keeps modernization efforts on track by ensuring that architectural choices, updated patterns, and new coding practices are documented and comprehended. Modernization demands knowledge continuity: when documentation is lacking or outdated, upgrades can become risky. Sunlight mitigates that risk by illuminating every path. Swimm guarantees that modern code does not turn into tomorrow's legacy burden. Heimdal creates a stable and protective environment. It safeguards endpoints, devices, and networks from attacks, ensuring that development and modernization occur in a clean, safe setting. Regardless of how advanced or secure the code may be, if the environment around it is at risk, the system can be exposed. Heimdal makes sure that old software on endpoints, compromised sessions, or threats at the network level do not endanger the internal modernization efforts taking place within the codebase. It keeps things stable while modifications are underway. When these factors align the core understanding, the growing capabilities, and the support from modern tools the whole system starts to develop with intention. This is what we call modernization driven by security. Modernization goes beyond just updating dependencies or rewriting code.
Modernization is the result of:
- recognizing weak patterns early,
- replacing outdated components safely,
- reorganizing structures without breaking integrity,
- removing risky or obsolete elements,
- and continuously implementing updated best practices.
All of this requires the balance and stability that the metaphorical tree represents. Without stability, modernization becomes risky, without nourishment, modernization becomes incomplete, without understanding, modernization becomes blind, the result of this balance is the fruit. Not a rushed or unstable output, but a reliable, secure, precise product shaped by:
- deep internal understanding of systems,
- consistently applied practical abilities,
- and modern tools that reinforce strong decisions at every stage.
Modern code comes from a balance that makes it cleaner, more updated, standardized, stronger, and in tune with today. The results are better when old code is swapped out, risky practices are eliminated, and new architectural ideas are embraced. This outcome shows not only modern features but also stability, resilience, security, and clarity in modern standards. A secure product isn't just about one part being great, its about all parts working together smoothly. The roots provide nourishment; the trunk gives support, the branches reach out, and the environment offers protection. Modernization flourishes naturally in this ecosystem. Security today follows this same pattern. It's not loud or flashy. It develops through repetition, familiarity, and the ability to spot problems early. It grows through many cycles of finding issues, improving, and strengthening. With the help of modern tools, the process of modernization becomes easier. Fixes happen quicker, patterns become more obvious, risk areas decrease, outdated parts get updated, legacy code gains structure, and systems grow with confidence instead of doubt. Growth doesn't come from just one source.
It comes from the continuous interaction between:
- steady internal clarity,
- adaptive problem-solving,
- strong, supportive tooling,
- and ongoing reinforcement that keeps improvement active.
This constant cycle understands, detect, modernize, stabilize, repeat is the true engine of secure modernization. This balance leads to secure, modern, efficient products results that are reliable, smooth, and resilient. Each iteration becomes stronger than the last, not because it was forced, but because it was grown with intention and sustained clarity. A tree does not announce how it grew; its strength is visible. Its fruit speaks for itself. Likewise, the most modern, secure systems are the outcome of environments where stable understanding, refined capability, and automated tools work quietly together creating software that feels effortlessly safe, thoroughly updated, and confidently modern.





