Updated: February 17, 2026
The Cybersecurity Maturity Model Certification (CMMC) is no longer a regulatory horizon — it is an active gating requirement embedded in live Department of Defense (DoD) contracts today. For defense contractors who have delayed their compliance journey, the window is rapidly narrowing. If your organization is pursuing DoD work and lacks current CMMC certification status, you may already be losing bids.
This guide covers the contracts and solicitations currently including CMMC language, what the phased rollout means for your organization in 2026, and the concrete steps you need to take right now to stay competitive in the Defense Industrial Base (DIB).
What Does It Mean When a DoD Contract Mentions CMMC?
CMMC is the DoD's unified cybersecurity certification framework, built upon the foundation of DFARS 252.204-7021 and NIST SP 800-171. It strengthens enforcement by requiring either self-assessments or third-party validated certification — depending on the sensitivity of the information your organization handles — as a condition for contract award.
As of November 10, 2025, the 48 CFR Final Rule took effect, formally authorizing DoD contracting officers to embed CMMC requirements directly into solicitations, task orders, and delivery orders. Contracting offices across the Navy, Army, Air Force, and broader DoD are already specifying CMMC Level 2 as a minimum requirement for competitive bids.
When CMMC language appears in a solicitation, it means your certification status must be current and visible in the Supplier Performance Risk System (SPRS) prior to award, a self-assessment or C3PAO third-party assessment is required based on your assigned CMMC level, and subcontractors flowing down CUI must meet equivalent certification requirements. If your SPRS profile does not reflect current certification, your bid may be rejected outright.
February 2026: Active Contracts & Solicitations with CMMC Requirements
Below is a snapshot of recent DoD contracts and solicitations published on SAM.gov that include active CMMC requirements. These examples span multiple military branches and reflect how broadly certification requirements have been deployed across the defense supply chain.
2/6/2026 — Cylindrical Antenna – Phase B System Department of the Navy, NAVAIR — Anticipates CMMC Level 2 (CUI). Offerors may contest the assigned level with written justification.
2/5/2026 — 3DH2-M O&TI Mapping Operations U.S. Army Geospatial Center & USACE — CMMC Level 2 (Self) minimum; C3PAO preferred for systems handling Controlled Unclassified Information (CUI).
2/5/2026 — DFSP Hachinohe Transformer Replacement NAVFAC — Requires a current CMMC Level 2 Self-Assessment posted in SPRS prior to award.
2/4/2026 — Site Lighting Conduits at 5 LFs Air Force Global Strike Command — Vendors must have a current NIST 800-171 Assessment or equivalent — a direct pathway aligned with CMMC Level 2 requirements.
2/3/2026 — Ship Self Defense System (SSDS) Legacy NAVSEA — CMMC Level 2 certification listed as a core capability requirement.
2/3/2026 — IDIQ MAC for Submarine Support NAVSEA — Requires the ability to undergo C3PAO assessment every three years for the duration of the contract.
2/2/2026 — Inert Warhead for RRPR Department of the Army — CMMC Level 2 or higher required prior to contract award.
These represent only a fraction of active solicitations. Hundreds of additional contracts issued in late 2025 and early 2026 reflect the same pattern, with requirements spanning Levels 1 and 2 tied to FCI and CUI handling across virtually every branch of the military.
Understanding the 2026 CMMC Phase Implementation Timeline
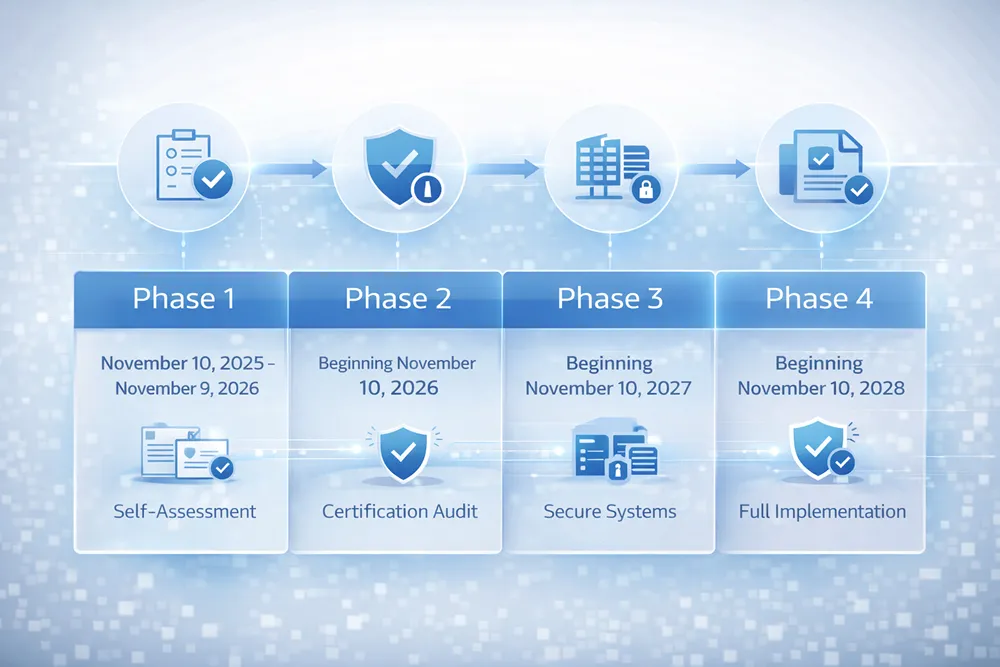
CMMC 2.0 is being rolled out in a structured four-phase approach. Understanding where we are today — and what is coming — is essential for planning your compliance strategy.
Phase 1 (November 10, 2025 – November 9, 2026): Currently active. CMMC Level 1 and Level 2 self-assessments are now a condition of award for applicable new DoD contracts. Contracting officers retain discretion to require C3PAO-assessed Level 2 at any time. The DoD estimates approximately 65% of the DIB is affected during this phase.
Phase 2 (Beginning November 10, 2026): Mandatory C3PAO-assessed Level 2 certification will be required in applicable solicitations and contracts. Level 3 requirements, assessed by DIBCAC, may also be incorporated at DoD's discretion.
Phase 3 (Beginning November 10, 2027): Level 2 certification requirements extend to existing contracts. Level 3 certification becomes mandatory for applicable high-sensitivity programs.
Phase 4 (Beginning November 10, 2028): Full implementation. CMMC requirements apply to all DoD contracts above the micro-purchase threshold where FCI or CUI is handled.
The critical takeaway: Phase 2 is less than nine months away. Given that Level 2 C3PAO readiness takes an average of 6 to 18 months, organizations that have not yet started their assessment journey are already at risk of missing that deadline.
Important February 2026 DFARS Regulatory Update
A significant regulatory change took effect February 1, 2026. DFARS 252.204-7019 has been formally deleted, and DFARS 252.204-7020 has been renumbered to 252.240-7997. The basic self-assessment and SPRS upload requirements under the legacy 7019/7020 framework have been eliminated. Contractors now fulfill all assessment obligations exclusively through CMMC under DFARS 252.204-7021. These changes are part of a broader FAR overhaul to remove regulatory redundancy. DFARS 252.204-7012 remains in effect and unchanged.
Why CMMC Level 2 Has Become the Baseline Standard for Defense Contractors
Across the majority of recent DoD solicitations, CMMC Level 2 — requiring protection of CUI and formal assessment against all 110 controls from NIST SP 800-171 — has emerged as the de facto standard for defense contractors. Three factors are driving this:
Scope of CUI handling is the first driver. Most meaningful DoD work involves creating, processing, or transmitting CUI — automatically placing contractors in the Level 2 category, regardless of organization size.
Prime contractor pressure is the second driver. Defense primes including Lockheed Martin, Boeing, and Northrop Grumman have already issued directives to their supply chains, requiring suppliers to document current CMMC status in SPRS and pursue C3PAO certification for CUI-handling systems — independent of specific contract language. Compliance with these directives is increasingly a condition of continued partnership.
C3PAO capacity constraints are the third driver. The number of certified third-party assessment organizations is currently limited relative to the roughly 80,000 contractors who will eventually require Level 2 certification. Early engagement is essential before Phase 2 demand surges.
Our CMMC preparation services are specifically designed to help defense contractors navigate both the technical requirements and the C3PAO assessment process efficiently.
The Cost of Non-Compliance: More Than a Missed Bid
For many contractors, the risk of CMMC non-compliance is framed purely as a potential loss of bid eligibility. But the consequences extend much further.
False Claims Act (FCA) exposure is one of the most significant risks. The CMMC Final Rule heightens potential FCA liability tied to inaccurate cybersecurity reporting. Contractors who submit inaccurate SPRS scores or misrepresent their certification status face significant legal and financial exposure — well beyond the loss of any individual contract.
Supply chain exclusion carries compounding downstream effects. Prime contractors are actively auditing their subcontractor supply chains. Being removed from a prime's approved vendor list can reshape an organization's entire government contracting portfolio — and that process is already underway ahead of Phase 2.
Competitive displacement accelerates over time. As CMMC compliance becomes universal across the DIB, non-compliant organizations will find themselves permanently locked out of a growing share of federal defense spending. Compliant competitors will capture those opportunities while uncertified vendors are systematically excluded.
The subcontractor cascade is often overlooked. Compliance requirements flow down from primes to subs. If your organization serves as a subcontractor, the prime is responsible for ensuring your CMMC status is current — and many are already cutting non-compliant vendors before Phase 2 formally begins.
Understanding how CMMC intersects with your broader vendor ecosystem requires a rigorous approach to third-party risk management — particularly for organizations with complex supply chains or multiple CUI-handling subcontractors.
What Level of CMMC Does Your Organization Need?
CMMC operates across three levels, each tied to the type and sensitivity of information your organization processes.
Level 1 — Foundational applies to contractors handling Federal Contract Information (FCI). It requires 17 basic cybersecurity practices aligned with FAR 52.204-21, fulfilled through annual self-assessment and SPRS submission.
Level 2 — Advanced applies to contractors managing Controlled Unclassified Information (CUI). It requires all 110 security requirements from NIST SP 800-171. High-priority contracts require C3PAO third-party assessment, with recertification every three years and annual affirmation of continuous compliance.
Level 3 — Expert applies to contractors working on the most sensitive DoD programs subject to Advanced Persistent Threat (APT) concerns. It requires all Level 2 controls plus 24 select NIST SP 800-172 requirements, with assessment conducted by DCMA's DIBCAC.
The CMMC level is determined by DoD program managers based on the nature of the acquisition and is specified in the solicitation. If you are uncertain which level applies, a formal gap assessment is the right first step.
How Long Does CMMC Compliance Actually Take?
This is where many contractors significantly underestimate the timeline. The average defense contractor requires 6 to 12 months to become assessment-ready for Level 2. Some organizations with more complex IT environments may require up to 18 months. A conditional certification requires a minimum score of 88 out of 110 (80%) under NIST 800-171A, and any Plan of Action & Milestones (POA&M) items must be closed within 180 days or the conditional certification expires.
Given the November 10, 2026 Phase 2 deadline, organizations that have not yet started their CMMC preparation are already working against the clock. The time to act is not Q3 2026 — it is today.
Key Steps to Achieve CMMC Readiness Before Phase 2
A structured approach reduces both timeline risk and assessment costs. The core preparation pathway covers these stages:
Step 1 — Determine Your CMMC Level: Review current and anticipated DoD contracts to identify what level applies based on the sensitivity of information you handle.
Step 2 — Define Your Compliance Boundary: Identify which systems, personnel, and facilities fall within scope. Organizations can limit their boundary through a secure CUI enclave, significantly reducing documentation and assessment complexity.
Step 3 — Conduct a Gap Assessment: Perform a formal gap analysis aligned with NIST SP 800-171 to identify control deficiencies and document findings in a System Security Plan (SSP).
Step 4 — Remediate Control Gaps: Implement missing or deficient controls. Prioritizing high-impact controls first accelerates your path to assessment readiness.
Step 5 — Submit Your SPRS Score: Upload your self-assessment score and executive affirmation to SPRS with accurate expiration dates and affirming official documentation.
Step 6 — Engage a C3PAO (for Level 2): For contracts requiring C3PAO assessment, engage a certified assessor early before Phase 2 demand surges.
Step 7 — Maintain Continuous Compliance: CMMC is not a one-time event. Implement continuous monitoring, conduct annual affirmations, and prepare for recertification every three years.
Our CMMC preparation services provide end-to-end support across each of these stages — from initial gap assessment through documentation, remediation, and C3PAO engagement.
CMMC and Third-Party Risk: Why Your Supply Chain Is Part of Your Compliance Obligation
A frequently overlooked dimension of CMMC compliance is supply chain security. The CMMC program explicitly requires prime contractors to ensure that subcontractors hold current certification at the appropriate level for information flowing down to them. Your compliance is not just about your own systems — it encompasses every vendor, subcontractor, and service provider that touches your CUI environment.
For organizations managing complex vendor ecosystems, this creates a significant due diligence obligation. Failing to vet subcontractor compliance status can expose the prime contractor to both contract disqualification and FCA liability. A structured third-party risk management program ensures your entire supply chain meets the CMMC requirements your contracts demand and that supplier compliance remains current through recertification cycles.
CISA's supply chain risk management guidance provides additional frameworks that complement CMMC requirements for organizations managing sensitive federal information across extended vendor networks.

Key Takeaways
- CMMC is already in contracts. Phase 1 has been active since November 10, 2025, and hundreds of active solicitations across the Navy, Army, Air Force, and broader DoD now include CMMC language.
- CMMC Level 2 is the baseline standard for contractors handling CUI, requiring all 110 NIST SP 800-171 controls and, in many cases, C3PAO third-party certification.
- Phase 2 begins November 10, 2026, mandating C3PAO-assessed Level 2 certification for applicable contracts. With a 6–18 month preparation timeline, there is no time to delay.
- A February 2026 DFARS update eliminated the 7019/7020 framework, consolidating all assessment obligations under DFARS 252.204-7021.
- Non-compliance carries compounding risks including FCA exposure, supply chain exclusion by defense primes, and permanent loss of bidding eligibility.
- Your subcontractor ecosystem is part of your compliance obligation, making a robust third-party risk management program essential.

%402x.svg)




%402x.svg)

